What are the key terms and acronyms Okta uses?
Active Directory (AD)
- (AD) is a directory service that Microsoft developed for the Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services.
Okta AD Agent
- A lightweight program that runs as a service outside of Okta.
- It is typically installed behind a firewall and allows Okta to tunnel communication between an on-premises service and Okta’s cloud service.
- Okta employs several agent types: Active Directory, LDAP, RADIUS, RSA, Active Directory Password Sync, and IWA. For example, users can install multiple Active Directory agents to ensure that the integration is robust and highly available across geographic locations. You can change these settings any time as you refine your Okta configuration.
App Integration Wizard (AIW)
- If the app that you want to add does not already exist within the Okta Integration Network (OIN), you can create one with AIW.
- The AIW allows you to create custom:
- SWA apps
- SAML 2.0 apps
- OIDC apps
- With immediate functionality
Attribute Level Mastery (ALM)
- Is an enhancement to the profile-mastering concept.
- ALM changes the profile-mastering model by allowing admins to override the source that masters the entire Okta user profile.
- When users are mastered by attribute, we call this attribute-level mastery.
- ALM delivers finer grain control over how profiles are mastered by allowing admins to specify different profile masters for individual attributes.
- Profile mastering only applies to Okta user profiles, not app user profiles.
Authentication
- Will allow users to enter our environment
- Example:
- Logging into a Windows workstation with a username and password.
- Your driver’s license identifies who you are based on several pieces of information.
- For a user to have access to our system, they must first authenticate in.
Authorization
- Determines what you can do in the system
- Example:
- When you log into your workstation, can you install apps or change your desktop wallpaper?
- You show your Driver’s license to the police officer to show that you are authorized to drive the vehicle
- But just because you have a driver’s license doesn’t mean you can drive a tank or a bus
Big Bang
- When an app is SAML enabled and turning on SAML turns off password authentication.
- This is an implementation scenario that cannot be a phased implementation, it is a moment in time where the application has a go-live.
- Big Bang adoption is a software migration method that involves getting rid of the existing system and transferring all users to the new system simultaneously.
- Implementation is faster with big bang adoption than other methods:
- Parallel adoption
- Phased adoption
- Pilot Conversions
- An Example of a Big Bang App is G Suite. If you pull up the Okta SAML documentation for G Suite you will see:
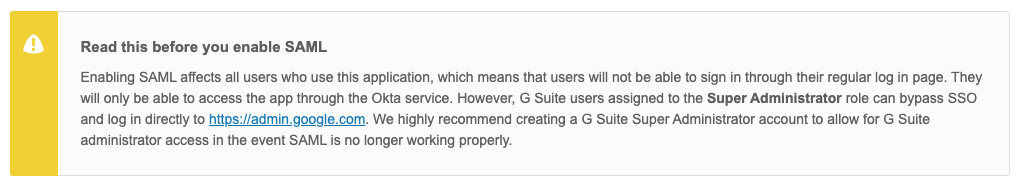
- This text is telling you that all users need to be imported into Okta to use this app. If they do not know about Okta it could cause confusion and they can get locked out of G Suite. Since this is an integral app in many companies' daily workflows, it is imperative that a company knows which apps are Big Bang. Iron Cove Solutions is an expert in handling G Suite Okta deployments. Contact us if you have any questions.
Blacklisting
- A Blocklist is a primary control mechanism that allows through all elements except those explicitly mentioned. Bring Your Own Device (BYOD)
Bring your own device (BYOD)
- Refers to the policy of permitting employees to bring personally owned devices (laptops, tablets, and smartphones) to their workplace, and to use those devices to access privileged company information and applications.
Chiclet
- The “buttons” that appear on an end user’s Homepage and represent each app for access through Okta
- Clicking the chiclet instantly signs in and authenticates users to the app
- Example:

CRM
- Customer relationship management (CRM) is a technology for managing all your company's relationships and interactions with customers and potential customers. The goal is simple: Improve business relationships.
CRUD
- Create, Read, Update, and Delete
Deep Linking
- The use of a hyperlink that links to a specific, generally searchable or indexed, a piece of web content on a website, rather than the websites’ home page
Downstream Application
- In the context of Okta provisioning, a downstream app is one that is receiving data from Okta.
End-User
- The people who have their own Okta home page (My Applications), with chiclets to authenticate into all apps.
- But do not have any administrative control.
Federated Identities
- In the IT world, a person can have many identities across different systems; it can be tough to deal with, and that’s where the concept of “federated identities” comes into play.
- Federated Identity is the linking of attributes across multiple systems.
- Example: using Facebook to log into Dig or Skype.
- We can reduce our electronic identities, and it reduces the need for multiple accounts across multiple platforms.
HR as a Master (HRaaM)
- Okta Lifecycle Management connects your HR system and IT resources to automate onboarding and to off board in a modern, seamless, and secure way.
- Okta Workday Consulting
Identity as a Service (IDaaS)
- IDaaS cloud-based authentication operated by a third-party provider.
Identity Management (IDM)
- Defines who you are, what you can do, and who you can interact with.
- This means your identity refers to your authentication, authorization, and privileges.
IDM Management Lifecycle
- Start of the IdM Lifecycle via manual or automated provisioning
- Then the user is configured for our environment
- The user can enter our environment, which is called authentication.
- Then we can determine what the user has access to, which is called authorization.
- We then need to maintain that user with continued support with the provisioning and deprovisioning of apps and systems.
- We can provide access to apps through self-service.
- When the relationship with the user ends, the user is deprovisioned.
- The rights are removed from the systems and apps they had rights to.
- Even though a user has been deprovisioned it is possible to provision them back into the system.
Identity Provider (IdP)
- It is a service that manages end-user accounts analogous to user directories such as LDAP and AD.
- And can send SAML responses to SPs to authenticate end-users (within this scenario, the IDP is Okta).
- https://developer.okta.com/docs/reference/api/idps/
Independent Software Vendor (ISV)
- Okta partners with various ISVs (usually producing enterprise applications) to integrate (with Okta):
- On premises
- In the cloud
- Or Native-to-mobile devices
- https://developer.okta.com/docs/guides/build-provisioning-integration/overview/
Integrated Windows Authentication (IWA)
- A Microsoft product that allows SSO via a Web Browser.
- https://support.okta.com/help/s/article/IWA-Troubleshooting-Guide
Kerberos
- A user enters credentials, and a ticket is issued.
- Ticket similar to a ticket you receive at the movies.
- You must provide that ticket to gain access to that theater.
- And with Kerberos you must provide that ticket to gain access to that system
- Kerberos
Lightweight Directory Access Protocol (LDAP)
- A lightweight client-server protocol for accessing directory services, specifically X.500-based directory services. LDAP runs over TCP/IP or other connection-oriented transfer services.
Mastered
- Where the profile is created and maintained.
- The authoritative source. Multi-Factor Authentication (MFA)
- MFA is an additional step to verify your identity when you sign in to an application. Using MFA keeps your account more secure, because it makes it more difficult for hackers to steal all the information necessary to impersonate you.
Okta Integrating Network (OIN)
- The OIN is comprised of thousands of public, pre-integrated business and consumer apps.
- As an on-demand-service, OIN integrations are continuously validated, always up to date, and continually growing both in number and capability. Open ID Connect (OIDC)
- Is an authentication layer on top of OAuth 2.0, an authorization framework.
- The standard is controlled by the OpenID Foundation.
Okta Verified
- Each app found in the Okta Applications page has either an Okta Verified, Community Created, or Company Verified designation. Okta Verified indicates that the app was created either from the OAN or by Okta community users, then tested and verified by Okta.
One Time Pass Token (OTP Token)
- A uniquely generated password that can only be used once. Org
- An abbreviation of organization.
- But can also be thought of as a company.
- A company that uses Okta as their SSO portal is generally referred to as an org.
- As an admin, you decide how Okta should be displayed and/or integrated with your org.
Organizational Unit (OU)
- Organizational units are AD containers into which you can place users, groups, computers, and other organizational units.
- It is the smallest scope or unit to which you can assign Group Policy settings or delegate administrative authority. Profile Master
- A profile master is an app (usually a directory service such as AD, or human capital management system such as Workday) that acts as a SOT for user profile attributes.
- A user can only be mastered by a single app or directory at any one time.
- There can only be one profile master that masters a user’s entire profile.
Provisioning
- The ability to automatically create, update, and deactivate a user in an application.
RADIUS client
- Is a RADIUS-enabled device at the network perimeter that enforces access control for users attempting to access network resources.
- Can be:
- VPN Server
- Wireless access point
- Network access server supporting dial-in modems
- Dial-in modem
Software as a Service (SaaS)
- A method of software delivery and licensing in which software is accessed online via a subscription, rather than bought and installed on individual computers.
Security Accounts Manager (SAM)
- The Security Accounts Manager is a database file in Windows that stores users' passwords.
Security Assertion Markup Language (SAML)
- SAML is an XML-based standard for exchanging authentication and authorization data between an IdP and a SP.
- The SAML standard addresses issues unique to the SSO solution and defines 3 roles:
- The end-user
- IDP
- SP
- A way to securely communicate credentials.
- There are 2 parties in a SAML agreement.
- The IDP
- And the SP
- Here’s how SAML works through Okta
- SP-initiated flow:
- The end-user requests (principally through a browser) a service from a SP.
- The SP request obtains an identity assertion from the IdP (in this case, Okta).
- On the basis of this assertion, the SP can decide whether or not to authorize or authenticate the service for the end-user.
- IdP-initiated flow:
- With Okta as the IdP, an end user goes to the Okta browser and clicks on a chiclet, sending a SAML Response to the configured SP.
- A session is established with the SP, and the end-user is authenticated.
- SP-initiated flow:
- For SAML apps, you need to search for Okta SAML documentation. Here is an example of Dropbox Okta SAML Instructions. Iron Cove Solutions is an expert in Dropbox deployments. Please contact us if you have any questions.
System for Cross-domain Identity Management (SCIM)
- An open standard that allows for the automation of user provisioning. SOW
- Scope of Work Single Source of Truth (SSOT)
- Information systems design and theory, a single source of truth (SSOT) is the practice of structuring information models and associated data schema such that every data element is stored exactly once. Smart Cards
- A card with the user's credentials.
- A card is inserted, don’t have to enter username/password, and the card has the user’s credentials. Soft-token
- A software-based security token that generates a single-use PIN.
- Hardware-based tokens are more secure but more expensive than soft-tokens.
Service Provider (SP)
- A Service Provider is a company, usually providing organizations with communications, storage, processing, and a host of other services.
- Within Okta, it is any website that accepts SAML responses as a way of signing in users.
- And has the ability to redirect a user to an IdP (e.g., Okta) to begin the authentication process. Secure Sockets Layer (SSL)
- SSL (Secure Sockets Layer) is a standard security protocol for establishing encrypted links between a web server and a browser in online communication. The usage of SSL technology ensures that all data transmitted between the web server and browser remains encrypted.
Single Sign-on (SSO)
- As an end user the ability to log in once and have access to other apps without having to enter credentials.
- From Admin standpoint, multiple ways to implement SSO:
- Kerberos
- Smartcards
- One time pass token OTP
- IWA
- SAML
- SWA
- Is an SSO system developed by Okta to provide single sign-on for apps that don’t support proprietary federated sign-on methods or SAML.
- Users can enter their credentials for these apps on their homepage.
- These credentials are stored such that users can access their apps without entering their credentials each time.
- When users first sign-in to an SWA app from their homepage, they see a pop-up message asking if they were able to sign-in successfully. Secure Web Authentication (SWA)
- For web applications that do not provide support for federated single sign-on Okta has developed our Secure Web Authentication (SWA) technology. Template App
- Is an app that can be used to create custom apps that are not in the OIN.
Virtual Private Network (VPN)
- A virtual private network (VPN) extends a private network across a public network. It enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
Whitelisting
- The practice of identifying entities that are provided a particular privilege, service, mobility, access or recognition. Entities on the list will be accepted, approved and/or recognized.
eXtensible Access Control Markup Language (XACML)
- The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies.
What Size Companies Do We Work With?
Okta for Enterprises (500+ Employees)
Our Enterprise Deployments of Okta are ideal for organizations with complex IT configurations. We provide the right Migration and Deployment packages for enterprises, leveraging deep expertise in identity management, access control, and integrations across various platforms. Our Enterprise Business package is cost-effective, ensuring secure, seamless identity management. We are experts in Okta.
Mid-Size Companies (51-500 Employees)
Growing organizations with complex operational needs and Companies expanding their market reach without the hassel of learning sophisticaed cloud service. Mid-market organizations face unique challenges in managing digital identities, security, and cloud infrastructure. A cloud managed service provider like Iron Cove specializes in Okta support can be a game-changer for businesses looking to optimize their identity management strategy.
Okta for Small Business (1-50 Employees)
Iron Cove Solutions is a trusted provider of Okta SSO identity solutions for small businesses. We offer tailored Deployment and Support packages designed specifically for small businesses. Our “Small Business Package” is affordable and structured to quickly set up your identity and access management within the Okta security cloud. We are experts in Okta deployments. This is great for Startups and local enterprises seeking scalable solutions. We are very cost-effective and agile support for your business needs.
Okta for Non-Profits - Any size
We help non-profit organizations implement Okta. As experienced Okta partners, we develop deployment plans tailored to your budget and specific needs, ensuring access to secure, affordable identity and access management solutions. We guide you through each step of working with Okta.
Okta Cloud Managed Support
Our Okta Cloud Managed Support services are designed to help organizations maintain a secure environment both during and after deployment. Whether you’ve already implemented Okta Cloud Security or are just beginning, we offer support packages that ensure businesses of all sizes have the security support they need.




