Leverage Okta Security Policies.
How can you leverage Okta's multi-tier, context-based security policies to enhance user access?
A common question that new customers of Okta ask us is how we should build out our sign-on and multi-factor policies. Although each industry has different compliance requirements, we have found an ideal design that helps get you started.
This guide will dive into the advantages of Multi-factor Authentication and Sign-On policies and share a configuration guide.
Advantages of Multi-factor Authentication
Multi-factor authentication provides an extra layer of security by requiring more than just a password to access your work apps. It helps prevent unauthorized access and protects you from common cyber attacks.
- Enhanced Security: By combining multiple verification forms, such as a password and a code sent to your phone, multi-factor authentication makes it more difficult for unauthorized users to access your accounts.
- Protection Against Data Breaches: If someone gets hold of your password, multi-factor authentication adds a barrier that makes it much harder for them to access your data, providing an extra layer of protection against data breaches.
- Compliance Requirements: Multi-factor authentication helps businesses meet compliance requirements for protecting sensitive information like customer data and financial records.
Sign-On Policies with Okta
The Okta sign-on policy determines who has access to Okta, where they can access it from, and how they must authenticate themselves. To create a sign-on policy, you need to create a policy and then add rules to it. By default, Okta provides one default sign-on policy, which you can customize and apply to all users in your organization. It acts as a catch-all policy for all users.
Okta tests sign-in attempts against policies in order from top to bottom until a policy is found that the attempt satisfies. Details such as group membership, network location, and behavior determine which policy to enforce.
Where to start?
As security approaches go through ebbs and flows, so do your sign-on policies. A perfect starting point is to create a High, Medium, and Low risk policy structure.
The following section references the Okta Identity Engine Dashboard.
In your Okta Admin Dashboard, go to Security and Global Sign-On Policies. There is only the 'Default Policy' by default, which you should review and modify. This policy will serve as your catch-all if a user cannot satisfy the new policies we will create.
- Create a High-Risk Policy - for this policy, we typically require MFA at every login and limit the default access to no more than an hour. Additionally, you want to add a step-up rule if new behavior is detected, such as a new device or IP address. Commonly, we enforce this policy on any admin or elevated access user such as a manager, accounting rep, or C-Suite level user or users traveling outside of trusted network zones.
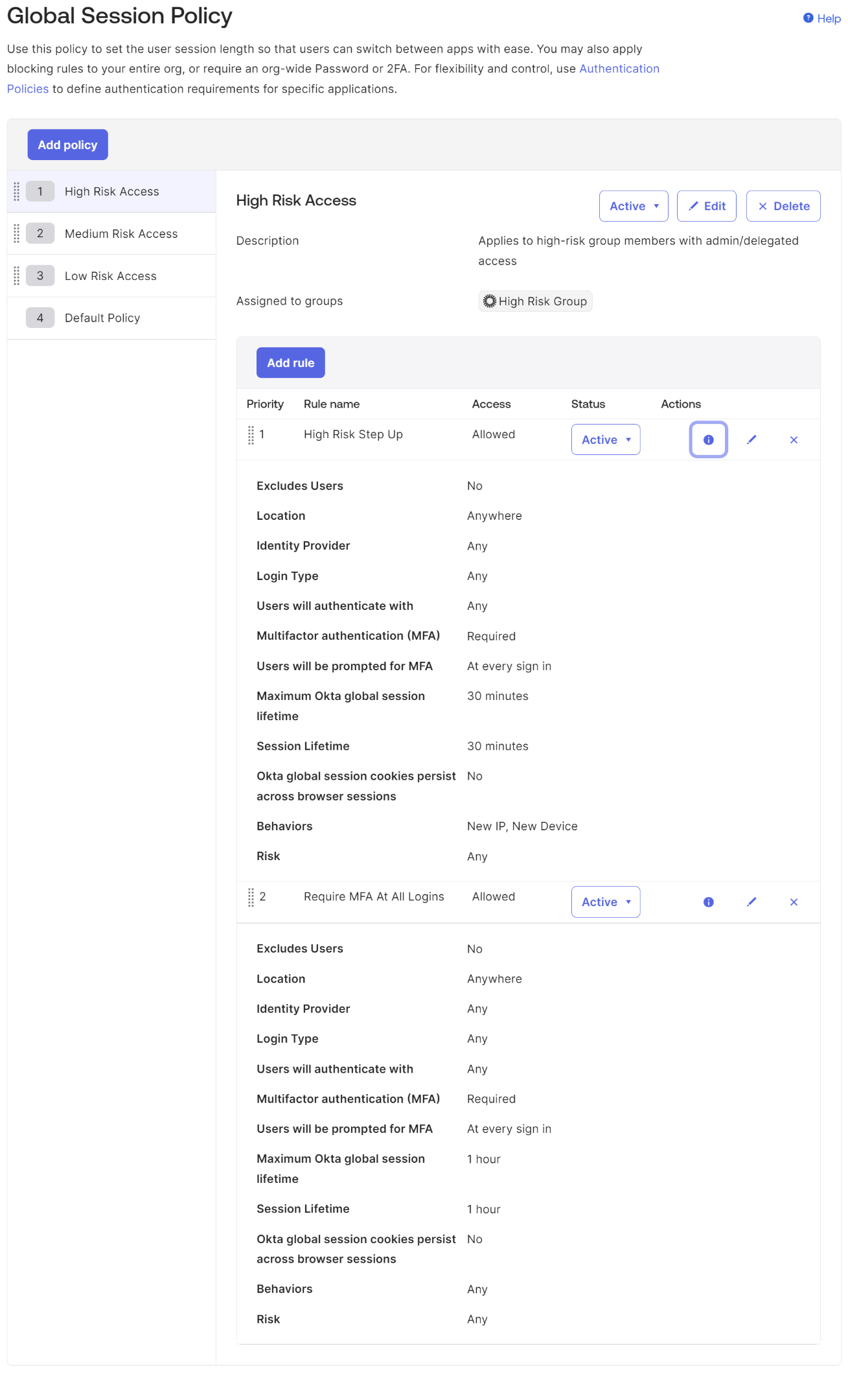
Create a Medium-Risk Policy - an extended session and idle time are set for this policy so that users aren't challenged at every login and can idle on their Okta dashboard for longer. A sweet spot for most customers is a 1-day global session with about 8 hours of idle time.
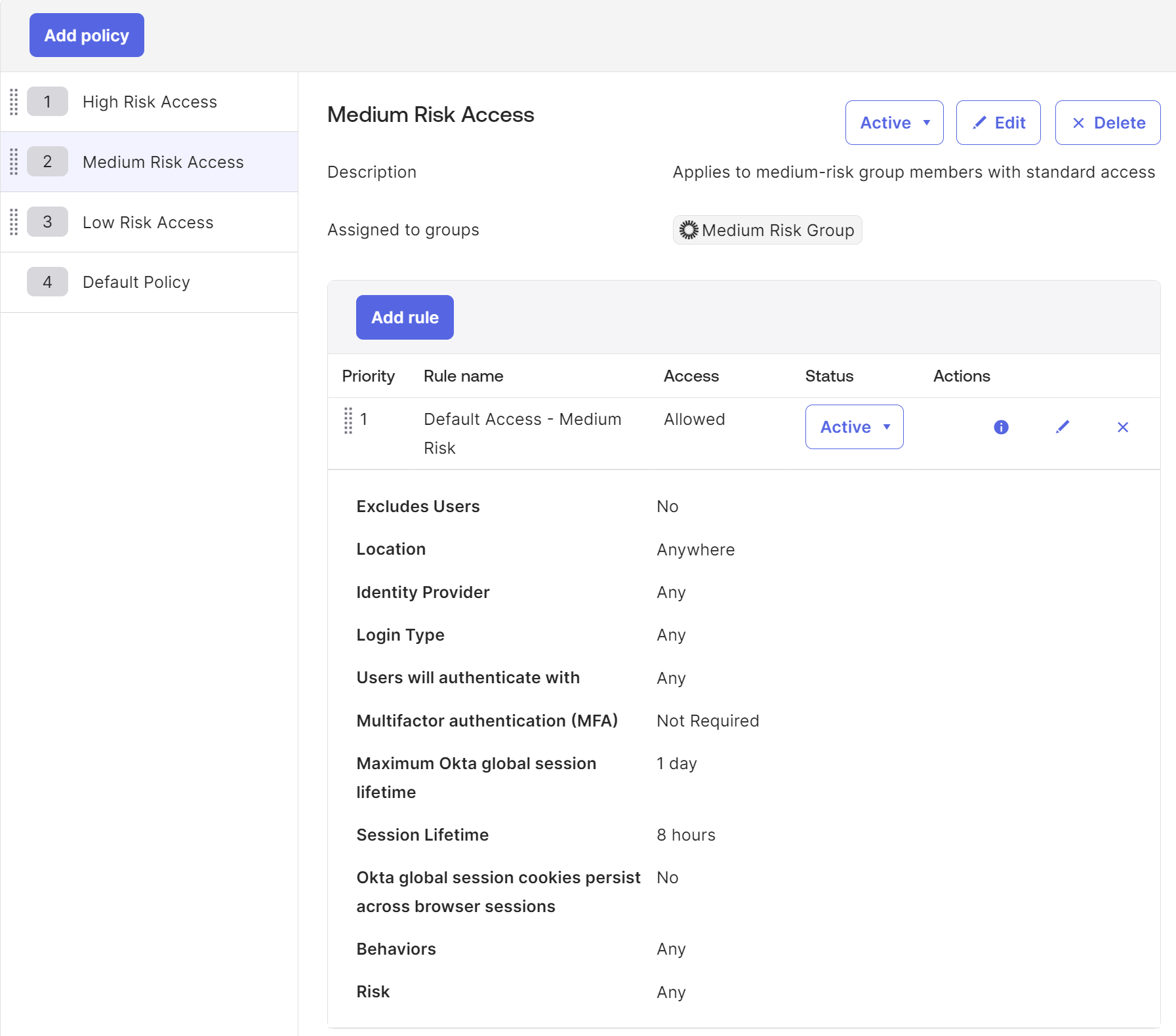
Create a Low-Risk Policy - for this policy, we have the freedom to grant an extended session to users. The main focus should be creating two or more rules focusing on network context - In-office vs. Out of Office. For example, we give In-Office users a single challenge for their entire workday, while Out of Office, the Okta session is extended to 4 hours maximum.
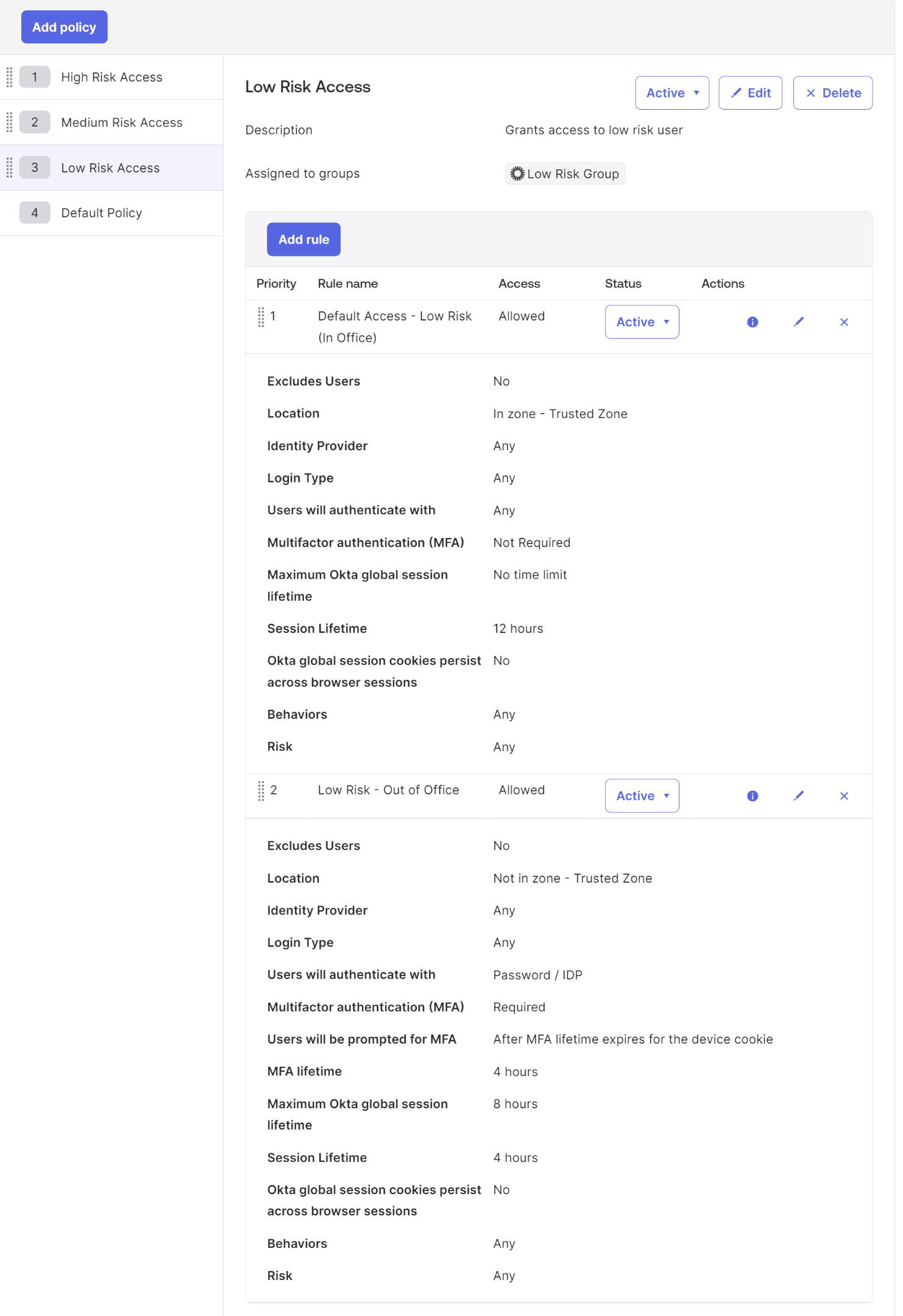
The High-Medium-Low Risk policy structure is an excellent way to ensure that your organization's internal departments follow the proper Multi-Factor Authentication and Session time protocols. By testing these rules in a preview or limited scope before enabling them org-wide, you can guarantee that your policies are triggering correctly. Setting up a lab instance and attempting a sign-in is an effective way to determine whether your policies are working correctly. It's always better to be confident in your policies before implementing them; this approach helps ensure your organization is secure.
If you require additional help, always contact our team of experts, ready to assist you with any Okta needs.
What Size Companies Do We Work With?
Okta for Enterprises (500+ Employees)
Our Enterprise Deployments of Okta are ideal for organizations with complex IT configurations. We provide the right Migration and Deployment packages for enterprises, leveraging deep expertise in identity management, access control, and integrations across various platforms. Our Enterprise Business package is cost-effective, ensuring secure, seamless identity management. We are experts in Okta.
Mid-Size Companies (51-500 Employees)
Growing organizations with complex operational needs and Companies expanding their market reach without the hassel of learning sophisticaed cloud service. Mid-market organizations face unique challenges in managing digital identities, security, and cloud infrastructure. A cloud managed service provider like Iron Cove specializes in Okta support can be a game-changer for businesses looking to optimize their identity management strategy.
Okta for Small Business (1-50 Employees)
Iron Cove Solutions is a trusted provider of Okta SSO identity solutions for small businesses. We offer tailored Deployment and Support packages designed specifically for small businesses. Our “Small Business Package” is affordable and structured to quickly set up your identity and access management within the Okta security cloud. We are experts in Okta deployments. This is great for Startups and local enterprises seeking scalable solutions. We are very cost-effective and agile support for your business needs.
Okta for Non-Profits - Any size
We help non-profit organizations implement Okta. As experienced Okta partners, we develop deployment plans tailored to your budget and specific needs, ensuring access to secure, affordable identity and access management solutions. We guide you through each step of working with Okta.
Okta Cloud Managed Support
Our Okta Cloud Managed Support services are designed to help organizations maintain a secure environment both during and after deployment. Whether you’ve already implemented Okta Cloud Security or are just beginning, we offer support packages that ensure businesses of all sizes have the security support they need.




